
Manufacturing is Being Threatened
Custom manufacturers today face a growing list of challenges, from supply chain disruptions to labor shortages. However, one of the most pressing and underestimated threats is cybercrime. As these manufacturers become increasingly reliant on connected technologies, such as ERP systems and shop floor automation, the risk of an attack disrupting operations or exposing sensitive data is higher than ever. Therefore, building cyber resiliency isn’t optional; it’s essential to protect your business, suppliers, and customers.
Recent Attacks Reveal What’s at Stake
Ransomware attacks targeting industrial sectors have increased over the years, resulting in widespread disruptions and significant financial losses. A recent Honeywell report found that these attacks increased by 46 percent from Q4 2024 to Q1 2025, with nearly 2,500 new incidents recorded during that short period alone.
Ransomware has evolved into a targeted weapon against industries like manufacturing, energy, and construction. In Honeywell’s 2025 cyber threat report, attacks against operational technology (OT) systems spiked dramatically, with USB-based malware still representing about 25% of the most severe threats.
For custom manufacturers, this type of attack could mean:
Production Downtime and Lost Revenue
When critical systems, such as ERP platforms or shop floor controllers, are encrypted or shut down, it can bring operations to a halt. Every hour of downtime is costly. Estimates suggest that unplanned downtime across Fortune 500 manufacturers costs around $1.5 trillion per year globally.

Ransomware attacks are on the rise for manufacturing companies. Not only are the companies at risk, but their customers and suppliers are too.
Theft of Intellectual Property
Make-to-order manufacturers often produce unique designs and customer-specific products. These proprietary assets, like blueprints, CAD files, and pricing models, are valuable targets for cybercriminals. Losing control of that data could erode competitive advantage and customer trust.
Disruption of the Supply Chain
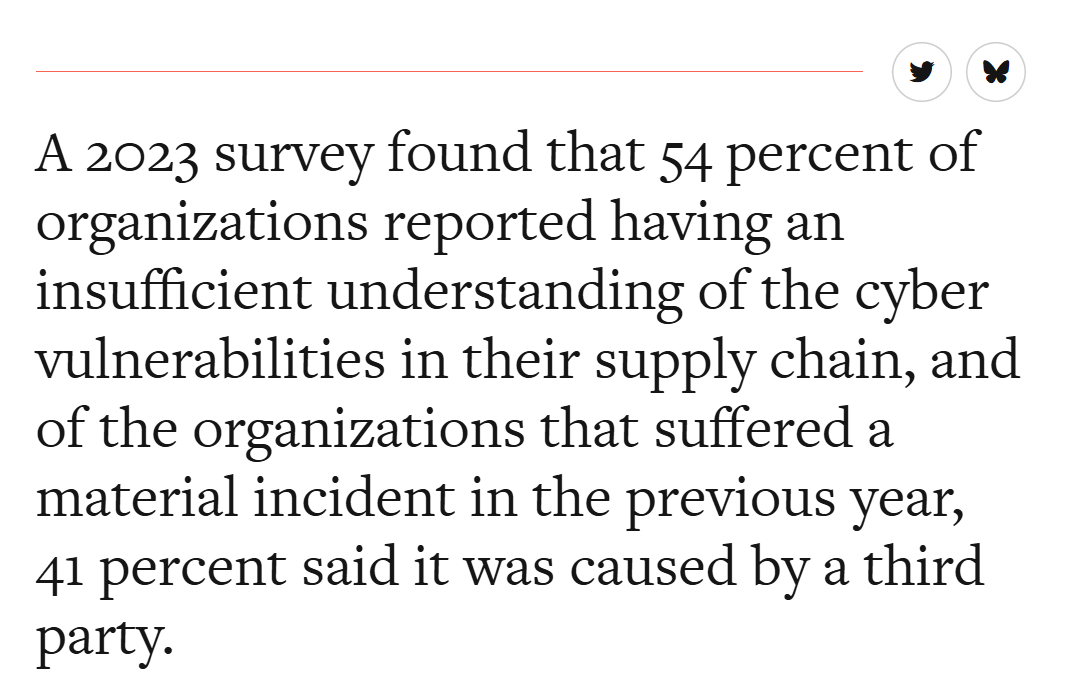
Modern manufacturing is deeply interconnected. A breach at one point in the chain can cause ripple effects across production and delivery schedules. Attackers frequently exploit weak links in third-party software or vendor connections to gain access to broader networks (Source: Elisa IndustrIQ).
Compliance and Regulatory Penalties
The good news is that the U.S. government is stepping in to assist with stronger cyber protections. New voluntary regulations, such as the U.S. Cybersecurity Performance Goals, guide manufacturers to follow stricter security practices to lessen their risk.
Safety Hazards
Cyberattacks targeting OT systems can have physical consequences like equipment malfunctions, process errors, or even workplace injuries. For custom manufacturers who depend on precision and coordination, compromised systems don’t just hurt productivity; they can endanger workers.
Practical Steps Toward Cyber Resiliency
Cyber resiliency means having the ability to prepare for, respond to, and recover from cyberattacks with minimal disruption. It involves more than antivirus software; it’s a whole business strategy. Here are some key ways custom manufacturers can build their defenses:
Use Trusted Security Standards to Guide Your Strategy
Cybersecurity frameworks can seem complex, but they offer a helpful roadmap for building better protection. Here are three widely adopted ones, explained in simple terms:
- IEC 62443 is like a safety manual for your machines and production systems. It helps manufacturers secure their equipment, separate critical systems from non-critical ones, and make sure vendors follow best practices, too.
- ISO 22301 is about making sure your business can bounce back if something goes wrong. It helps you plan for emergencies by identifying critical areas, setting recovery goals, and making sure teams are trained and ready.
- NIST Cybersecurity Framework offers a five-step guide: Identify what’s at risk, Protect it, Detect if something goes wrong, Respond quickly, and Recover fully. It’s a flexible tool for manufacturers of all sizes.
You don’t have to follow every piece of every framework, but using them as a foundation can help you identify where your weaknesses are and how to fix them.
(Source: American Progress Organization)
Strengthen Supply Chain Security
Many cyberattacks begin with customers, suppliers, or vendors. Manufacturers should:
- Evaluate partners’ cybersecurity practices before signing contracts.
- Add security requirements to supplier agreements.
- Continuously monitor for signs of vulnerability or breach.
This ensures that your business isn’t brought down by someone else’s weak defenses (Source: TechRadar).
Design Security into Your Systems
The earlier you consider security, the better. This principle, called “security by design,” means building systems with security features from the start, not adding them later. For example:
- Limit access to sensitive data only to people who need it.
- Encrypt information traveling between systems.
- Use multi-factor authentication for logins.
- Patch software vulnerabilities regularly.
By designing systems to be secure, you reduce the chance that a hacker can break in or cause damage.
Build a Cyber Incident Response Plan
Planning for an attack is just as important as trying to prevent one. This includes:
- Identifying what systems are most critical to your operations.
- Setting recovery goals, such as how fast you need systems back online.
- Practicing your response, just like a fire drill.
- Knowing who’s responsible for what during a breach.
Having a solid plan can mean the difference between a one-day delay and a weeks-long shutdown.
Train Your Workforce
Technology isn’t your only line of defense. People play a big role in stopping cyber threats. Train your team to:
- Recognize phishing emails and suspicious activity.
- Safely handle USB devices and other portable media.
- Report issues quickly so problems can be addressed fast.
Cyber resiliency is a culture, one that starts from the top and includes everyone, from IT to the shop floor.
Frontier ERP Helps Your Company Stay Cyber Resilient

Cybersecurity isn’t just for large-volume manufacturers. Smaller manufacturers should also take steps to make their company more cyber resilient and eliminate potential threats.
Frontier ERP is designed to meet the security and operational needs of custom manufacturers. With secure architecture and built-in best practices, Frontier helps reduce your cyber risk and prepare you to respond if something goes wrong.
Features include:
- Role-based access controls that limit who can view or change critical data
- Full activity logs and change tracking for transparency
- Secure backup and disaster recovery capabilities
- Data encryption and compliance with frameworks like NIST and IEC 62443
Whether you’re a small shop or a multi-site manufacturer, Frontier ERP can help you create a more secure, cyber-resilient operation—without adding IT overhead.
Conclusion: Cyber Resiliency is Not Optional
Cyber threats to manufacturers are real, rising, and rapidly evolving. From lost revenue to damaged reputation and safety issues, the risks are too great to ignore. But custom manufacturers can take control by building a cyber resiliency plan that includes strong security standards, supplier oversight, incident response, and employee training.
Solutions like Frontier ERP help make this possible by integrating security into your everyday operations, so you can focus on running your business without fear of disruption.
Now is the time to take action, because being cyber resilient is no longer a luxury. It’s a necessity. For more information or to schedule a demo, click the link below or attend our August webinar.




